Electronic Team uses cookies to personalize your experience on our website. By continuing to use this site, you agree to our cookie policy. Click here to learn more.
Passwordless authentication is any identity verification system that doesn't require the use of a password. While it won't make conventional password-based authentication fizzle out in an instant, some passwordless authentication solutions have been developed to help enterprises simplify their transition to total passwordless authentication.
Speaking of passwordless authentication, it can come in the form of any/combination of physical security keys, biometrics, specialized apps, facial recognition, email magic links, etc. While different passwordless authentication solutions implement these authentication methods differently, they all share a set of key goals: provide a better user experience, ameliorate user identity management, and generally improve security.
This article explains everything you need to know about passwordless authentication and how to make the most of it for your business.
A notable disadvantage of password-based authentication is its vulnerability to attacks targeted at the weakest link in the security chain; that is, the end users. Users can easily forget their passwords, prompting them to use the same passwords they use on other platforms.
What this translates to is that any security compromise on one of these platforms leaves others who share the same password vulnerable. Let’s not forget that hackers can also obtain the passwords of end users via brute force and social engineering. There are hardly any instances where attacks stem from security holes found in an enterprise's security system. The end users are mostly the point of attack.
By going passwordless, you tackle these problems and stand to gain much more. Although multi-factor authentication is sometimes added to passwords to strengthen security, it only makes the already inconvenient passwords even more complicated, whereas passwordless authentication gives you the perfect balance between high security and convenience.
One major perk of passwordless authentication over the password-based ones is that it isn't knowledge-based, so users don't risk losing access to their accounts if they forget their passwords.
The importance of passwordless authentication cannot be adulated in any cloud environment. Not only does it provide end users with the much-needed security-centric convenience, but it can also increase the productivity of your IT staff and simplify their job.
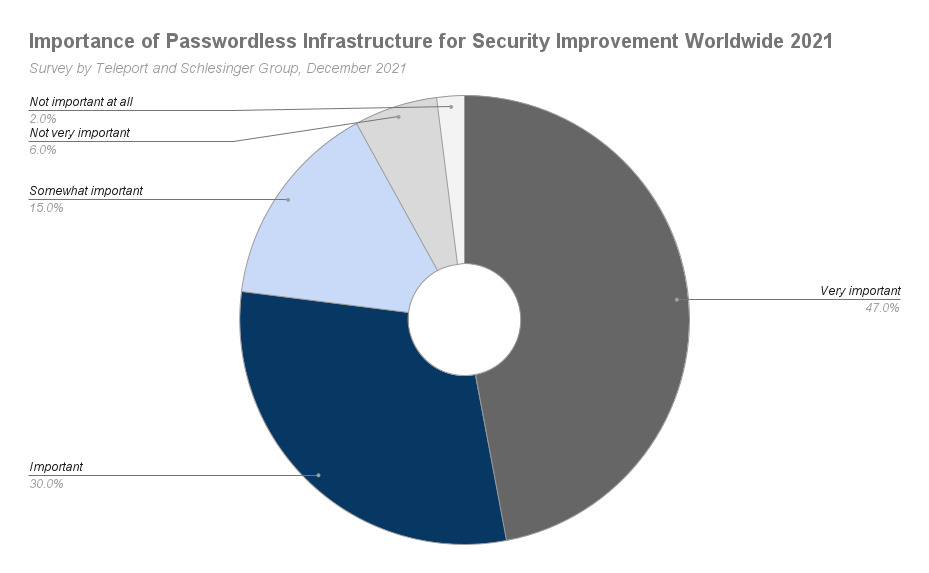
According to a worldwide survey conducted by Teleport Schlesinger Group, 47% of the 1,000 correspondents consisting of IT, devs, and security professionals agree that passwordless authentication is 'very important' to improve security. Another 30% echoes its importance, albeit on a slightly lower scale.
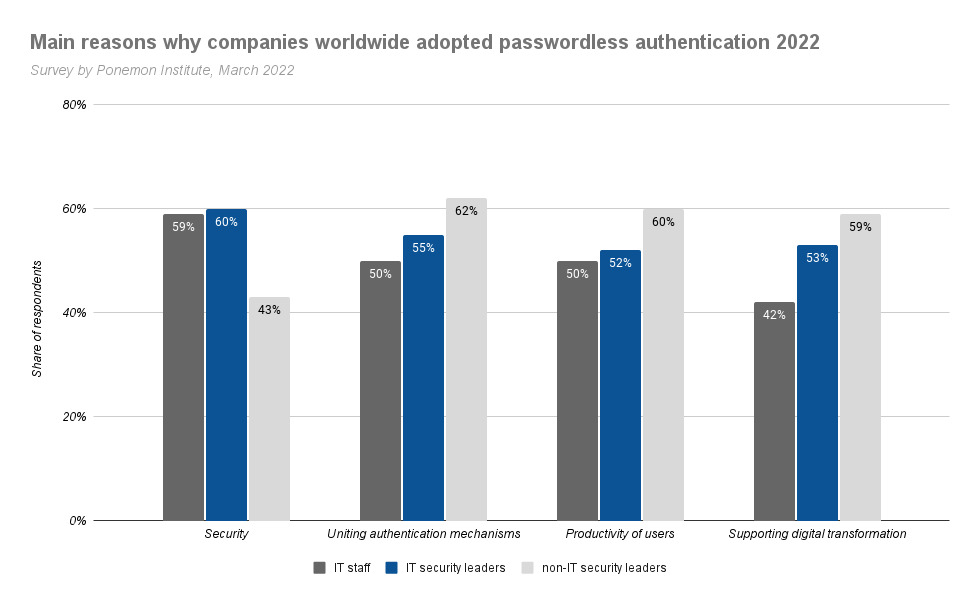
Meanwhile, another survey conducted by Ponemon Institute, and published by Nok Nok reveals the importance of passwordless authentication in aiding user productivity, uniting authentication mechanisms, among other benefits. The survey, which has 1,007 correspondents, consists of IT staff, IT security leaders, and non-IT security leaders.
IT staff and security leaders alike agree that passwordless authentication could indeed help strengthen security by eliminating password memorization. Also, Non-IT security leaders attest that it increases users' productivity and unites existing authentication mechanisms.
Upscaling password-based security systems has always been a daunting task for IT departments, compelling them to add piecemeal elements to their identity stack as security needs continue to evolve. Passwordless authentication resolves this issue by simplifying regulatory requirements and the implementation of MFA. This translates to fewer elements needed to attain the desired results.
Lastly, the user productivity favored in the survey could also result in more revenue for companies as customer attrition sees a significant decrease. "A third of customers will discard their carts online if they forgot their passwords", according to MasterCard. By simplifying identity management for customers through passwordless authentication, their chances of coming back to complete their purchase of your product/service increases.
There has been a growing misconception about what true passwordless authentication should function like. While some passwordless authentication companies may position themselves as passwordless, they are sometimes just built on password-based architecture and don't align with Fast Identity Online 2 (FIDO2), which characterizes a true passwordless authentication. While some passwordless authentication companies don't develop their solutions to require traditional passwords, the metrics they use for authentication can still be considered password-based.
Such metrics are:
While positioned as passwordless, these above methods defeat the idea of passwordless authentication, which is improved security. A hacker can redirect OTPs sent to a SIM via SMS with man-in-the-middle or smishing attacks. The same can be said for a magic link, which anyone with the account to which it's sent can access it.
This begs the question, what is true passwordless authentication, and how does passwordless authentication work? Passwordless authentication methods that meet industry standards are:
This type of authentication grants access to users based on scanning or verification of biological characteristics such as Iris, fingerprint, voice, face, etc. It is one passwordless authentication method that reduces user friction greatly and is virtually impossible for hackers to imitate.
Certificate-based passwordless authentication replaces the traditional password with a digital certificate which is provisioned onto an end user's mobile device. It then serves as a user's trusted digital identity.
This passwordless authentication method replaces a password with a peripheral device (such as a USB dongle) inserted into a user's device upon request. Depending on the security mechanics of the host, this triggers a limited session where a user is required to confirm a code displayed on the screen.
Some USB dongles have an embedded LCD screen and, as such, can display crucial passcodes required to complete the login session.
Passwordless authentication serves the same purpose as passwords, which is to grant users access to a service or cloud resources only after they complete a challenge. The major difference is that the challenge this time comes in the form of biological characteristics verification or interaction with a piece of hardware.
Speaking of biological characteristics, users must verify them by utilizing the biometrics reader embedded in the endpoint device, which could be a fingerprint reader, voiceprint, retina scanner, or face recognizer. The face recognition projects and analyzes thousands of invisible dots to establish a depth map and capture an infrared image of the user. Therefore, software-based face readers found on some mobile devices don't count.
Meanwhile, fingerprint scanning involves using a print sensor on your device to capture high-resolution images of your fingerprint. Interestingly, depending on the underlying technology of the sensor, it can analyze the subepidermal layers of the skin, read the fingerprints in 360-degree orientation, and categorize each print into a loop, arch, or whorl categories.
The focal points of these security methods are their high accuracy and personalization, which make duplicating, mimicking, or bypassing them virtually impossible. They get even more secure when they meet FIDO2 standards, thus preventing users' private data from being shared, transmitted, or stored in a database.
Passwordless authentication examples that meet FIDO2 standards are.
Passwordless Authentication has proven to be a better way to secure user identity, protect cloud resources, and generate even more revenue. The reduced user friction and convenience will spur them to keep coming back to use your services. As the market continues to grow, different passwordless authentication providers will continue devising means to make it work even more seamlessly with existing hardware. Most authentication as a service providers also provide Passwordless Authentication as their main authentication methods.
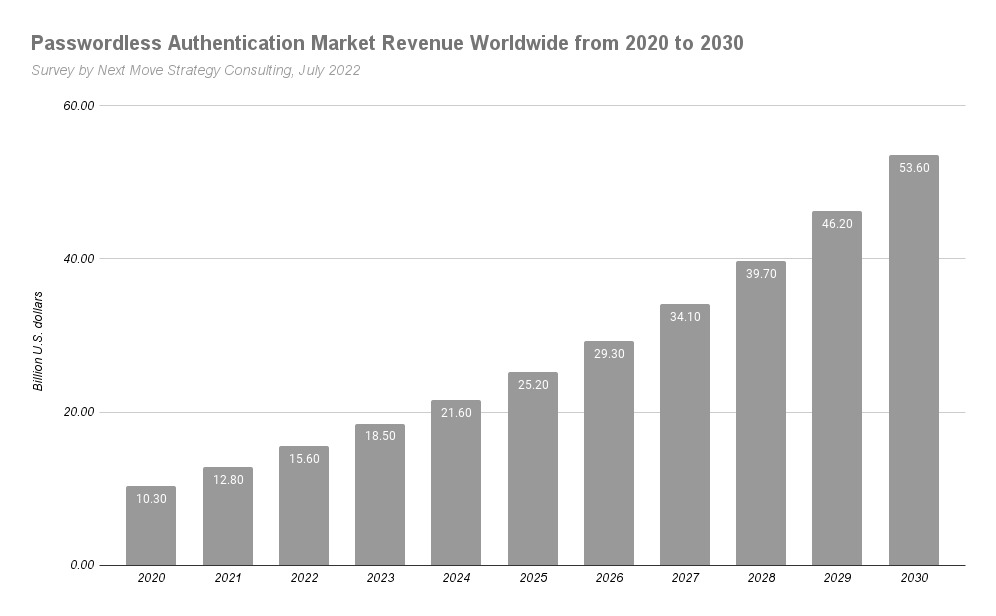
A recent survey by Next Move Strategy Consulting projects its worldwide revenue to hit well over 50b dollars by 2030 from its current $15.6b, which itself is quite a jump from the $10b in 2020. It can only get better.